Overview
AppArmor (Application Armor) is a Linux security module (LSM) that provides mandatory access control (MAC) for programs.
MAC is a security model where access to resources (files, directories, network ports, etc.) is strictly controlled by a central policy.It restricts programs’ capabilities with per-application profiles, helping to confine them and limit the damage that could be done by vulnerabilities or misconfigurations.
Key Concepts of AppArmor
-
Profiles: Each application or process has a profile that defines what files and capabilities it can access.
-
-
Profiles can be in enforce mode (violations are blocked) or complain mode (violations are logged but allowed)
-
AppArmor restricts applications based on profiles, even if you run them as root.Although root has full system access, but AppArmor controls what an application (even one run by root) can do.
-
-
- Path-based: AppArmor enforces security policies based on file paths.
- Kernel Integration: AppArmor is implemented in the Linux kernel and is available in major distributions like Ubuntu, Debian, and SUSE.
How AppArmor Works
- Profile Creation: You write a profile describing what a program can do (read/write files, execute, access network, etc.).
- Load into Kernel: Profiles are loaded into the kernel using tools like apparmor_parser.
- Enforcement: When the program runs, the kernel checks its actions against the profile.
- Logging: Violations (or permitted actions in complain mode) are logged via dmesg or /var/log/syslog.
Common Commands
- View status: sudo apparmor_status
- Generate a new profile: sudo aa-genprof /path/to/program
- Load a profile: sudo apparmor_parser -r /etc/apparmor.d/profile
- Put a profile in complain mode: sudo aa-complain /etc/apparmor.d/profile
- Enforce a profile: sudo aa-enforce /etc/apparmor.d/profile
Use Cases
AppArmor is particularly useful for hardening Linux systems by restricting what applications can do, based on defined security policies.
1. Hardening Network-Exposed Services
Use Case:
- Confining web servers, databases, or mail servers to reduce risk from vulnerabilities.
Examples:
- Apache/Nginx: Prevent from accessing /home, mounting devices, or executing binaries outside /usr/sbin/.
- MySQL: Restrict it to its own data directory.
- Postfix/Dovecot: Limit filesystem access to mail directories only.
Benefit:
- Even if the service is exploited (e.g., via a remote code execution bug), the damage is limited.
2. Protecting Sensitive Directories
Use Case:
Prevent critical folders (e.g., backups, configuration, source code) from deletion or tampering by specific apps.
Examples:
- Restrict cron, rsync, or other utilities from touching /etc/secure/ or /home/user/code/.
- Constrain backup tools so they can only read specific folders and not write anywhere else.
Benefit:
- Avoids unintended corruption, deletion, or ransomware-style attacks.
3. Running Untrusted or 3rd-party Binaries
Use Case:
- Isolate programs downloaded from the internet or developed by unknown parties.
Examples:
- Downloaded command-line tools
- Student code or automation scripts
- Old or legacy software that hasn’t been audited
Benefit:
- If the tool tries to access critical files or network resources, it’s blocked.
4. Apparmor in containers
Use Case:
- AppArmor helps you control what a container is allowed to do — like which files it can read or write, and whether it can use the network.
- Containers don’t access what they shouldn’t
Examples:
- Web Server Container (like Nginx)
- Allow: Read /var/www/html
- Deny: Writing to /etc/ or accessing /home/
- Prevents a hacked web server from damaging your system files.
- Database Container
- Allow: Access to /var/lib/mysql
- Deny: Everything else
- Limits database activity to its own data folder only.
Benefits:
- Security Isolation: Stops containers from harming your system
- Fine-Grained Control: Allow only what’s needed, block the rest
- Monitoring: See what containers try to access with logs
- Attack Protection: Helps block container escapes or malware
5. Creating a Secure Development/Test Environment
Use Case:
- Limit access for development tools or test scripts to avoid data loss or leaks.
Examples:
- Confine compilers or test runners to only touch /tmp and /home/user/project/.
- Block debug tools from accessing /proc/ or other process data.
Benefit:
- Minimizes risk from mistakes during testing or CI pipelines.
Installing AppArmor
AppArmor is usually pre installed on Ubuntu and Debian.
If not installed, you can install it with:
sudo apt update
sudo apt install apparmor apparmor-utils
sudo systemctl enable apparmor
sudo systemctl start apparmor
AppArmor Practical Example
Let’s imagine we have a text file with your grandma’s secret cake recipe that you don’t want a program to modify.
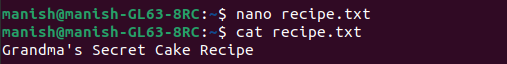
1. At first we create a file named recipe.txt
echo “Grandma’s Secret Cake Recipe”
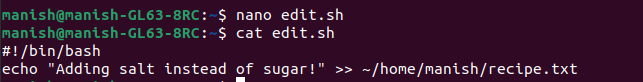
2. And now, imagine someone writes a simple program (edit.sh) that tries to modify your recipe:
#!/bin/bash
echo “Adding salt instead of sugar!” >> ~/recipe.txt
3. Generate AppArmor profile
sudo aa-genprof ~/home/ubuntu/edit.sh
When it says:
Please start the application to be profiled another window and exercise its functionality now.
4. Run this in another terminal:
./edit.sh
Then, back in the profiling window:
- Press S (Scan)
- Then F (Finish)
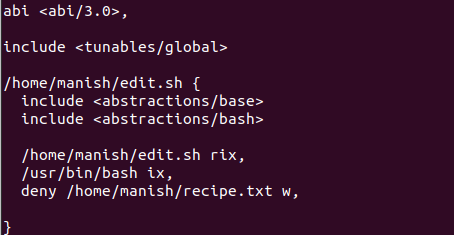
5. Edit the Profile to Deny Recipe Access
sudo nano /etc/apparmor.d/home.ubuntu.edit.sh
Add following line inside the {} block
deny /home/ubuntu/recipe.txt w,
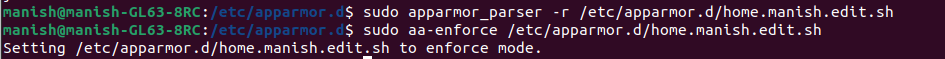
6. Reload and Enforce the Profile
sudo apparmor_parser -r /etc/apparmor.d/home.ubuntu.edit.sh
sudo aa-enforce /etc/apparmor.d/home.ubuntu.edit.sh
7. Run edit script again:
./edit.sh
You’ll see:
bash: /home/ubuntu/recipe.txt: Permission denied
And if you check the file recipe.txt :
It’s untouched!
Grandma‘s recipe is safe
8. You can also confirm Denial in Logs
journalctl | grep apparmor | tail -n 10
Conclusion
AppArmor is a powerful and easy-to-use Linux security tool that helps you control what applications and scripts can access on your system. Whether you’re protecting sensitive files, restricting untrusted scripts, or securing containers, AppArmor acts like a set of guardrails that enforce the principle of “least privilege.”

